- Retrait gratuit dans votre magasin Club
- 7.000.000 titres dans notre catalogue
- Payer en toute sécurité
- Toujours un magasin près de chez vous
- Retrait gratuit dans votre magasin Club
- 7.000.0000 titres dans notre catalogue
- Payer en toute sécurité
- Toujours un magasin près de chez vous
Sécurité du réseau
-
Hacking
Alex Wagner
- Livre broché | Anglais | 3 Manuscripts
- Book 1 - The Ultimate Guide to Hacking using 17 Most Dangerous tools This book will focus on some of the most dangerous hacker tools that are favourit... Savoir plus
69,95 €Livraison sous 1 à 4 semaines69,95 €Livraison sous 1 à 4 semaines -
Understand, Manage, and Measure Cyber Risk
Ryan Leirvik
- Livre broché | Anglais
- When it comes to managing cybersecurity in an organization, most organizations tussle with basic foundational components. This practitioner's guide la... Savoir plus
62,45 €Livraison 2 à 3 semaines62,45 €Livraison 2 à 3 semaines -
Hacking APIs
Corey J Ball
- Livre broché | Anglais
- Hacking APIs is a crash course in web API security testing that will prepare you to penetration-test APIs, reap high rewards on bug bounty programs, a... Savoir plus
83,45 €Livraison 1 à 4 semaines83,45 €Livraison 1 à 4 semaines -
Digital Fortress
Mahmoud Taha
- Ebook | Anglais
- Cybersecurity is the practice of protecting systems, networks, and programs from digital attacks. These attacks often aim to access, change, or destro... Savoir plus
9,49 €Disponible immédiatement9,49 €Disponible immédiatement -
Cybersecurity for Beginners
Attila Kovacs
- Livre relié | Anglais | How to Defend Against Hackers & Malware | n° 3
- Do you want to know what Critical Responsibilities a Cybersecurity Specialist have? Do you want to know what tools and techniques are used in Cybersec... Savoir plus
48,45 €Livraison 2 à 3 semaines48,45 €Livraison 2 à 3 semaines -
Cyberpocalypse
Matthew J Surburg
- Livre broché | Anglais
- Pay up or shut down. You choose. Cybercrime is on the rise and hackers have moved on from targeting individuals to targeting corporations both large a... Savoir plus
22,45 €Livraison 2 à 3 semaines22,45 €Livraison 2 à 3 semaines -
SpamAssassin
Alistair McDonald
- Livre broché | Anglais
- In depth guide to implementing antispam solutions using SpamAssassin .Implement the right antispam solution for your network and your business require... Savoir plus
43,45 €Livraison 1 à 2 semaines43,45 €Livraison 1 à 2 semaines -
Windows APT Warfare
Sheng-Hao Ma
- Livre broché | Anglais
- Learn Windows system design from the PE binary structure to modern and practical attack techniques used by red teams to implement advanced prevention ... Savoir plus
61,45 €Livraison 2 à 3 semaines61,45 €Livraison 2 à 3 semaines -
Pki
Andrew Nash, Derek Brink, Bill Duane
- Livre broché | Anglais
- This is a guide to implementing and understanding PKI technology. It features case studies of PKI implementation and deployment, and provides a step-b... Savoir plus
53,45 €Livraison sous 1 à 4 semaines53,45 €Livraison sous 1 à 4 semaines -
Nokia Firewall, Vpn, and Ipso Configuration Guide
Andrew Hay, Keli Hay, Peter Giannoulis
- Livre broché | Anglais
- "While Nokia is perhaps most recognized for its leadership in the mobile phone market, they have successfully demonstrated their knowledge of the Inte... Savoir plus
64,95 €Livraison 1 à 2 semaines64,95 €Livraison 1 à 2 semaines -
Engineering Trustworthy Systems: Get Cybersecurity Design Right the First Time
O Sami Saydjari
- Livre broché | Anglais
- Publisher's Note: Products purchased from Third Party sellers are not guaranteed by the publisher for quality, authenticity, or access to any online e... Savoir plus
101,45 €Livraison 2 à 3 semaines101,45 €Livraison 2 à 3 semaines -
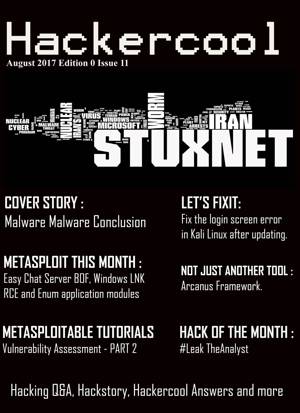
Hackercool Aug 2017
kalyan chinta
- Ebook | Anglais
- Here's what you will find in the Hackercool August 2017 Issue . 1. Malware Malware (Conclusion) : Cover Story : Worms, Spyware, Keylogger, Logic Bomb,... Savoir plus
4,20 €Disponible immédiatement4,20 €Disponible immédiatement -
Network Security and Data Privacy in 6G Communication
- Livre relié | Anglais | Wireless Communications and Networking Technologies
- The text presents a systematic review of the opportunities and existing security/privacy concerns in the 6G communications system. It further discusse... Savoir plus
259,45 €Livraison 2 à 3 semaines259,45 €Livraison 2 à 3 semaines -
Mommy! There's a Monster in our Computer
N K McCarthy
- Livre broché | Anglais
- The book that every parent should read to their child before they go on the Internet. The odds are very good that your child will not be negatively im... Savoir plus
24,95 €Livraison 2 à 3 semaines24,95 €Livraison 2 à 3 semaines -
Hands-on Penetration Testing for Web Applications: Run Web Security Testing on Modern Applications Using Nmap, Burp Suite and Wireshark (English Edition)
Richa Gupta
- Ebook | Anglais
- Learn how to build an end-to-end Web application security testing framework KEY FEATURES ● Exciting coverage on vulnerabilities and security loopholes... Savoir plus
13,99 €Disponible immédiatement13,99 €Disponible immédiatement -
Okta Administration
Lovisa Stenbäcken Stjernlöf, Henkjan de Vries
- Livre broché | Anglais
- Plan, design, and implement identity and access management solutions with Okta Key Features Learn how to use Okta for complete identity and access man... Savoir plus
50,45 €Livraison 1 à 2 semaines50,45 €Livraison 1 à 2 semaines -
RMF Security Control Assessor NIST 800-53A Security Control Assessment Guide
Bruce Brown, CISSP
- Ebook | Anglais | NIST 800 Cybersecurity
- Master the NIST 800-53 Security Control Assessment. The last SCA guide you will ever need, even with very little experience. The SCA process in laymen... Savoir plus
31,99 €Disponible immédiatement31,99 €Disponible immédiatement -
NIST Cybersecurity Framework (CSF) For Information Systems Security
Bruce Brown, CISSP
- Ebook | Anglais | NIST Cybersecurity Framework (CSF)
- Do you want to learn one security framework that helps you MASTER ALL frameworks? The NIST Cybersecurity Framework (CSF) is designed in such a way tha... Savoir plus
17,49 €Disponible immédiatement17,49 €Disponible immédiatement -
The Cloud Security Ecosystem
Raymond Choo, Ryan Ko
- Livre broché | Anglais
- Drawing upon the expertise of world-renowned researchers and experts, The Cloud Security Ecosystem comprehensively discusses a range of cloud security... Savoir plus
203,95 €Livraison 2 à 3 semaines203,95 €Livraison 2 à 3 semaines -
Security, Privacy, Trust, and Resource Management in Mobile and Wireless Communications
- Livre relié | Anglais | Advances in Information Security, Privacy, and Ethics
- While security is of vital importance to ensure the integrity of communications in wireless and mobile networks, most businesses which rely on these n... Savoir plus
314,45 €Livraison 2 à 3 semaines314,45 €Livraison 2 à 3 semaines -
Industrial Cybersecurity
Anand Shinde, Bipin Lokegaonkar
- Ebook | Anglais
- This book "Industrial Cybersecurity", offers an in-depth exploration of essential strategies for safeguarding industrial operations. It includes insig... Savoir plus
8,99 €Disponible immédiatement8,99 €Disponible immédiatement -
Advances in Cryptology - Eurocrypt 2015
- Livre broché | Anglais | Lecture Notes in Computer Science | Security and Cryptology | n° 9057
- The two-volume proceedings LNCS 9056 + 9057 constitutes the proceedings of the 34th Annual International Conference on the Theory and Applications of ... Savoir plus
105,45 €Livraison sous 1 à 4 semaines105,45 €Livraison sous 1 à 4 semaines -
Internet Security You Can Afford the Untangle Internet Gateway
Christopher Dawson, Dawson
- Livre broché | Anglais
- This text serves as the perfect reference tool for readers who understand end-user IT, hardware, and operating systems, but who have limited experienc... Savoir plus
39,45 €Livraison 1 à 2 semaines39,45 €Livraison 1 à 2 semaines -
Cybersecurity for Information Professionals
- Livre broché | Anglais
- The book is an introduction to essential concepts of cybersecurity and information security and the methods and techniques used to combat cybersecurit... Savoir plus
59,45 €Livraison 1 à 2 semaines59,45 €Livraison 1 à 2 semaines